SSH Mac, or Secure Shell on macOS, is a powerful tool for securely connecting to remote servers and managing them from your Mac. It provides a secure, encrypted connection, protecting your data and commands from prying eyes. Whether you’re a developer, system administrator, or simply need to access files on a remote machine, SSH Mac offers a reliable and efficient solution.
This comprehensive guide will delve into the world of SSH on macOS, covering everything from basic setup and configuration to advanced techniques like tunneling and remote desktop access. We’ll explore the security benefits of SSH, discuss best practices for securing your connections, and provide troubleshooting tips for common issues.
Introduction to SSH
SSH, or Secure Shell, is a network protocol that enables secure communication between two computers. It provides a secure channel over an unsecured network, like the internet, to allow users to access remote systems and execute commands as if they were logged in directly.
SSH is essential for secure remote access and administration of servers and other devices. It is widely used by system administrators, developers, and other professionals who need to manage and interact with remote systems securely.
Security Benefits of SSH
SSH provides a number of security benefits over other remote access methods, such as Telnet.
- Data Encryption: All data transmitted over an SSH connection is encrypted, making it impossible for unauthorized individuals to intercept or read the data.
- Authentication: SSH uses strong authentication mechanisms to verify the identity of both the client and the server. This prevents unauthorized access to the remote system.
- Integrity: SSH uses cryptographic techniques to ensure the integrity of the data transmitted over the connection. This prevents malicious modifications of data by third parties.
Common Uses of SSH
SSH has numerous applications in various scenarios, including:
- Remote Server Administration: System administrators use SSH to manage and administer remote servers, such as installing software, configuring services, and troubleshooting issues.
- Secure File Transfer: SSH can be used to securely transfer files between computers using the SFTP (Secure File Transfer Protocol) protocol.
- Remote Command Execution: SSH allows users to execute commands on a remote system as if they were logged in directly.
- Remote Access to Applications: SSH can be used to access remote applications, such as databases and web servers, securely.
Connecting to Remote Servers
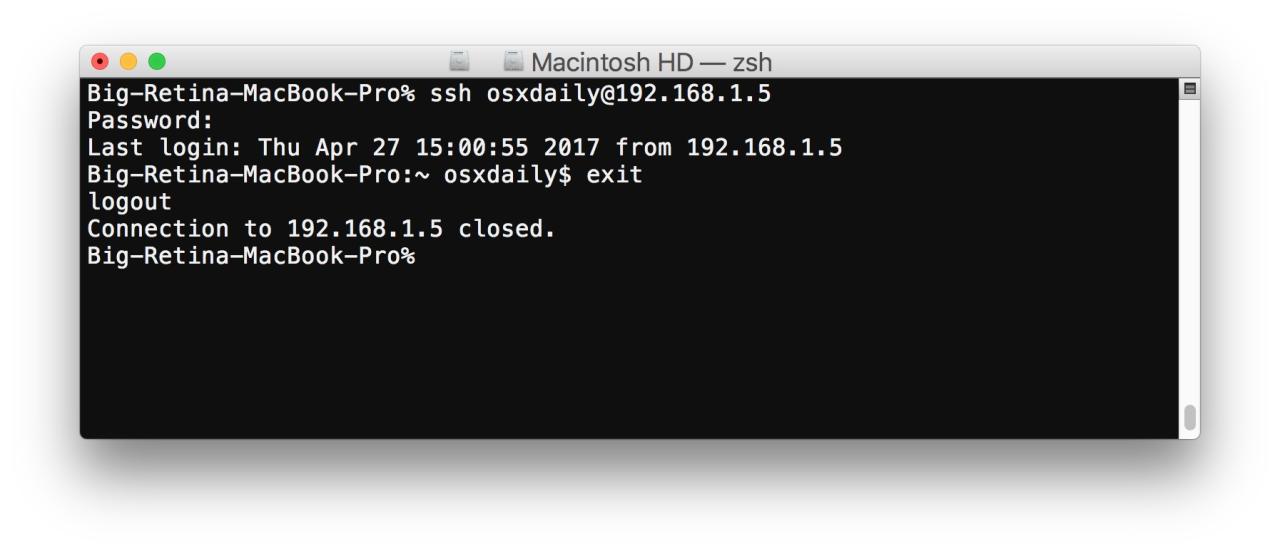
Connecting to a remote server using SSH allows you to manage and access resources on a machine that is not your local computer. This is done by establishing a secure connection, enabling you to execute commands and transfer files between your local machine and the remote server.
Using SSH Client Software
SSH client software acts as an intermediary, facilitating the connection between your local machine and the remote server. One popular SSH client for Mac is Terminal, which is already included in macOS. Terminal allows you to enter commands to establish and manage SSH connections.
Steps to Connect to a Remote Server Using SSH
- Open Terminal: Launch the Terminal application on your Mac.
- Enter the SSH Command: Type the following command, replacing “username” with your remote server username and “server_address” with the server’s IP address or domain name:
ssh username@server_address
- Authenticate: When prompted, enter your password for the remote server. If you have set up SSH keys for authentication, you might not need to enter a password.
- Access the Remote Server: Once connected, you will be presented with the remote server’s command prompt, allowing you to execute commands and interact with the server.
Common SSH Commands for Remote Management
Here are some common SSH commands used for managing remote servers:
- ls: List the files and directories in the current directory.
- cd: Change the current directory.
- pwd: Display the current working directory.
- mkdir: Create a new directory.
- rm: Remove a file or directory.
- scp: Securely copy files between your local machine and the remote server.
- sftp: Access files on the remote server through a secure file transfer protocol.
SSH Tunneling
SSH tunneling is a powerful technique that allows you to establish a secure connection between two points, even if they are not directly connected. This secure connection can be used to access resources on a remote network, bypass firewalls, or even create a secure connection between two devices.
Types of SSH Tunnels
SSH tunnels can be categorized into two main types:
- Forward Tunneling: This type of tunnel forwards traffic from a local port on your computer to a remote port on a server. This is useful for accessing services that are not accessible directly from your local network, such as a web server running on a remote server.
- Reverse Tunneling: This type of tunnel forwards traffic from a remote port on a server to a local port on your computer. This is useful for accessing services that are running on your computer from a remote network, such as a web server running on your computer.
Examples of Using SSH Tunnels
SSH tunnels are used in various scenarios, including:
- Secure Access to Remote Resources: If you are working from home and need to access resources on a company network, you can use an SSH tunnel to establish a secure connection between your computer and the company’s network. This allows you to access resources as if you were physically connected to the company network.
- Bypass Firewalls: SSH tunnels can be used to bypass firewalls that block access to specific ports or services. For example, if a firewall is blocking access to a web server on a remote network, you can use an SSH tunnel to establish a connection to the server and access the web server through the tunnel.
- Secure Communication Between Two Devices: SSH tunnels can be used to establish a secure connection between two devices, even if they are not directly connected. This is useful for creating a secure connection between two devices on different networks, such as a server and a desktop computer.
SSH for File Transfer
SSH, in addition to providing secure remote access, also offers reliable methods for transferring files between your local machine and remote servers. This functionality is particularly useful for managing files on web servers, sharing data with collaborators, or backing up critical information.
SFTP and SCP Protocols
SSH leverages two primary protocols for secure file transfer: SFTP (Secure File Transfer Protocol) and SCP (Secure Copy Protocol). Both protocols utilize SSH’s secure connection to ensure data integrity and confidentiality during file transfers.
SFTP is a file transfer protocol that operates over an SSH connection. It provides a more comprehensive set of features compared to SCP, including the ability to create, delete, and rename files and directories on the remote server. SFTP is often accessed through graphical file transfer clients or command-line utilities like `sftp`.
SCP, on the other hand, is a simpler protocol that focuses solely on copying files between local and remote systems. It’s commonly used for transferring files using the `scp` command in the terminal.
Transferring Files Securely Using SSH
Transferring files using SSH is a straightforward process, involving a few key steps:
– Establishing an SSH connection: Initiate an SSH connection to the remote server using the `ssh` command.
– Using SFTP or SCP: Once connected, you can use either SFTP or SCP to transfer files.
– Specifying file paths: Provide the full paths to the files you want to transfer on both the local and remote systems.
Using SFTP
To transfer files using SFTP, you can use the `sftp` command in your terminal. Here’s an example:
`sftp user@remote_server`
This command establishes an SFTP session with the remote server. Once connected, you can use SFTP commands to transfer files, such as:
`put local_file remote_file`
This command uploads the `local_file` to the remote server and saves it as `remote_file`.
Using SCP
To transfer files using SCP, you can use the `scp` command. Here’s an example of uploading a file to a remote server:
`scp local_file user@remote_server:remote_directory`
This command copies the `local_file` to the `remote_directory` on the remote server.
To download a file from a remote server, use the following command:
`scp user@remote_server:remote_file local_directory`
This command downloads the `remote_file` from the remote server and saves it in the `local_directory`.
Examples of File Transfer Using SSH
Let’s explore a few practical scenarios where SSH file transfer comes in handy:
– Uploading a website to a web server: Using SCP, you can securely transfer website files from your local machine to the web server, ensuring that your website content is accessible to visitors.
– Downloading log files from a remote server: You can use SCP to download log files from a remote server for analysis or troubleshooting purposes, ensuring the integrity of the data.
– Sharing large datasets with collaborators: SFTP allows you to securely share large datasets with collaborators, ensuring that the data is protected during transmission.
SSH for Remote Desktop Access
SSH, traditionally used for secure shell access and file transfers, can also be leveraged for remote desktop access. This functionality allows you to control a graphical desktop environment on a remote server, enabling you to run applications and manage the system visually.
X11 Forwarding
X11 forwarding enables the display of graphical applications running on a remote server on your local machine. It achieves this by establishing a secure connection between the remote server and your local X server.
- The remote server, upon receiving a request for an X11-enabled application, forwards the display requests to your local X server.
- Your local X server then renders the application’s graphical output on your screen.
Enabling X11 Forwarding
To enable X11 forwarding, you need to add the -X flag to your SSH command:
ssh -X username@remote_server
This tells the SSH client to establish an X11 forwarding connection.
Configuring X11 Forwarding
You can further customize X11 forwarding by using the following options:
-Y: Enables trusted X11 forwarding, allowing applications on the remote server to access local resources, such as files and devices. This option should be used with caution as it poses a security risk.-x: Enables X11 forwarding with authentication, requiring the user to provide a password or authentication token for each connection.
Using SSH for Graphical Applications
Once X11 forwarding is enabled, you can launch graphical applications on the remote server and view them on your local machine. For instance, to open a graphical terminal on the remote server:
ssh -X username@remote_server gnome-terminal
This command will launch a gnome-terminal instance on the remote server, and the terminal window will appear on your local machine.
Advanced SSH Concepts: Ssh Mac
SSH, beyond its basic functionality, offers powerful features for managing remote systems and data securely. This section delves into advanced SSH concepts, exploring how to leverage these capabilities for enhanced control and efficiency.
Port Forwarding
Port forwarding allows you to establish connections between a local port on your machine and a remote port on a server. This is particularly useful for accessing services that are not directly accessible from the outside, such as internal web servers or databases.
- Local Port Forwarding: Forwards traffic from a local port to a remote port on the server. This allows you to access services running on the server from your local machine as if they were running locally.
Example: To access a web server running on port 8080 on a remote server, you can forward traffic from your local port 8080 to the server’s port 8080.
- Remote Port Forwarding: Forwards traffic from a remote port on the server to a local port on your machine. This allows you to access services running on your local machine from the remote server.
Example: To access a database running on your local machine from a remote server, you can forward traffic from the server’s port 3306 to your local port 3306.
- Dynamic Port Forwarding: Forwards traffic from any local port to a specified remote port on the server. This allows you to access any service running on the server from your local machine.
Example: You can use dynamic port forwarding to access any service running on a server behind a firewall.
SSH Multiplexing
SSH multiplexing allows you to create a single persistent SSH connection that can be used for multiple sessions. This reduces the overhead of establishing multiple connections, resulting in faster access to remote systems.
- To enable multiplexing, use the `-M` flag when connecting to the server. This will create a single persistent connection that can be used for multiple sessions.
Example: `ssh -M -N user@server`
- Once the connection is established, you can use the `-t` flag to create a new session within the existing connection.
Example: `ssh -t -M -N user@server`
SSH Agent
The SSH agent is a program that stores your SSH keys securely, eliminating the need to enter your passphrase for every connection. This simplifies the authentication process and enhances security.
- To use the SSH agent, you need to add your SSH keys to the agent’s keychain.
Example: `ssh-add ~/.ssh/id_rsa`
- Once your keys are added to the agent’s keychain, you can connect to remote servers without entering your passphrase.
Example: `ssh user@server`
Troubleshooting SSH Connections
It’s not uncommon to encounter issues while connecting to a remote server via SSH. This section delves into common SSH connection errors and offers troubleshooting tips to help you resolve connection problems.
Common SSH Connection Errors and Their Causes, Ssh mac
Understanding the causes of SSH connection errors is crucial for effective troubleshooting. Here’s a breakdown of common errors and their potential reasons:
- Connection Refused: This error signifies that the remote server is not accepting SSH connections. The server might be down, have its SSH service disabled, or have a firewall blocking SSH traffic.
- Host Key Verification Failed: This error arises when the SSH client cannot verify the server’s public key. This can occur due to a mismatch between the server’s key and the client’s known hosts file or a security configuration issue.
- Permission Denied (publickey,password): This error indicates that the SSH client cannot authenticate with the server using the provided authentication method (public key or password). Check your SSH configuration, username, and password, or ensure the server is configured to accept the specified authentication method.
- Network Connectivity Issues: Network problems, such as a disconnected internet connection or a firewall blocking SSH traffic, can prevent successful SSH connections. Verify your network connection and check for any firewall rules that might be blocking SSH traffic.
- Incorrect Port Number: SSH connections typically use port 22. If the remote server uses a different port, ensure that you specify the correct port number in your SSH command.
Troubleshooting Tips for Resolving Connection Issues
Once you’ve identified the potential cause of the SSH connection error, you can implement the following troubleshooting steps:
- Verify Network Connectivity: Ensure that you have a stable internet connection and that your network is not blocking SSH traffic. You can use tools like ping or traceroute to check network connectivity to the remote server.
- Check Server Status: Confirm that the remote server is running and that the SSH service is enabled. You can try connecting to the server using a different SSH client or check the server’s logs for any errors.
- Review SSH Configuration: Ensure that your SSH client and server configurations are correct. Verify the username, password, port number, and authentication method. You can also check for any typos or errors in the configuration files.
- Verify Firewall Rules: Ensure that your firewall (local and remote) is not blocking SSH traffic. You may need to add a rule to allow SSH connections on the specified port.
- Check for Known Hosts File Issues: If you encounter a “Host key verification failed” error, examine your SSH client’s known hosts file. The file contains a list of known servers and their public keys. If the server’s key has changed or is not in the file, you may need to update or remove the entry.
- Consider SSH Tunneling: If your connection is blocked by a firewall or network restriction, you can use SSH tunneling to establish a secure connection. SSH tunneling allows you to forward traffic through a secure SSH connection, bypassing network restrictions.
Verifying SSH Configuration
It’s essential to verify your SSH configuration to ensure it’s correctly set up. You can use the following methods:
- SSH Client Configuration: Check the configuration file of your SSH client (e.g., ~/.ssh/config) for any settings related to username, password, port number, and authentication methods. Make sure these settings match the remote server’s configuration.
- Server Configuration: If you have access to the remote server, examine its SSH configuration file (e.g., /etc/ssh/sshd_config) to verify settings such as port number, authentication methods, and allowed users.
- Known Hosts File: Review the known hosts file (e.g., ~/.ssh/known_hosts) to ensure it contains the correct public key of the remote server. If the server’s key has changed, you may need to update or remove the entry.
SSH Alternatives
While SSH is a widely used and robust protocol for secure remote access, there are other alternatives that offer unique features and advantages. Let’s explore some of these options and compare them to SSH.
Mosh
Mosh, short for Mobile Shell, is a remote terminal application designed to provide a more seamless and responsive experience, especially over unstable or high-latency networks. Unlike SSH, which relies on TCP connections, Mosh utilizes UDP for communication.
Here are some key differences between SSH and Mosh:
- Connection Stability: Mosh excels in handling network interruptions and fluctuations. It can seamlessly reconnect to a remote server even if the connection is temporarily lost, making it ideal for mobile or unstable network environments.
- Latency Tolerance: Mosh is designed to minimize the impact of latency. It uses a technique called “latency-aware buffering” to predict user input and display output more smoothly. This is particularly beneficial for users with high-latency connections.
- Cross-Platform Support: Mosh is available on various operating systems, including Linux, macOS, and Windows, providing wide compatibility.
Mosh is an excellent choice when dealing with unreliable or high-latency network connections, offering a smoother and more responsive remote terminal experience.
Secure Shell
Secure Shell, commonly known as SSH, is a widely adopted protocol for secure remote access. It allows users to establish encrypted connections to remote servers, enabling secure command execution, file transfer, and remote desktop access.
SSH’s primary advantages include:
- Security: SSH encrypts all communication between the client and server, protecting sensitive data from eavesdropping and tampering.
- Versatility: SSH supports a wide range of functionalities, including remote command execution, file transfer (using SFTP or SCP), and secure remote desktop access (using X11 forwarding).
- Ubiquity: SSH is widely supported on various operating systems and platforms, making it a standard tool for system administrators and developers.
However, SSH can be less forgiving when dealing with unstable network connections, as it relies on TCP for communication.
Final Wrap-Up
Mastering SSH Mac empowers you with the ability to manage remote systems securely and efficiently. From simple file transfers to complex remote administration tasks, SSH provides a robust and versatile tool for interacting with remote servers. By following the best practices Artikeld in this guide, you can ensure secure and reliable connections, safeguarding your data and maintaining control over your remote resources.
SSH is a powerful tool for remotely accessing and managing your Mac, but sometimes you might need to work with a database on the server. If you’re looking for a robust database solution, consider using Microsoft SQL Server, which you can download from this website.
Once you’ve got SQL Server set up, you can use SSH to connect to the server and manage your database remotely, making your workflow even more efficient.
